Have you ever wondered if your cellular data is secure? Well, let’s dive into the world of encryption and find out if your phone’s data is protected. So, is cellular data encrypted? Let’s explore!
When we talk about encryption, we mean protecting our data by converting it into a secret code. Just like a lock and key, encryption ensures that only authorized parties can access our information. But what about our cellular data? Is it encrypted too? Let’s find out!
In this article, we’ll unravel the mystery behind cellular data encryption. We’ll discuss what encryption means for your mobile device, how it works, and most importantly, whether you can trust that your data is safe. So, keep reading and get ready for a journey into the fascinating world of cellular data encryption!
Is Cellular Data Encrypted?
Cellular data encryption is a crucial concern in today’s digital world. While wireless carriers claim to implement encryption protocols, it’s essential to understand the level of security provided. By encrypting cellular data, it becomes more challenging for unauthorized parties to access and decipher sensitive information.
However, the effectiveness of encryption can vary depending on the network and device. It is always advisable to use additional security measures such as VPNs to safeguard your data further.
Importance of Cellular Data Encryption
Cellular data encryption plays a crucial role in ensuring the security and privacy of our online communications. Encryption is the process of converting data into a format that is indecipherable to unauthorized individuals, making it secure from interception and eavesdropping.
Without encryption, our sensitive information, such as passwords, credit card details, or personal messages, could be easily accessed by hackers or malicious actors.
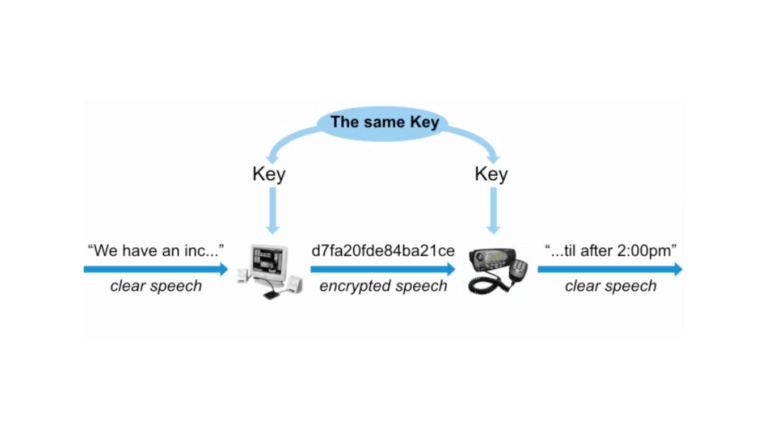
When cellular data is encrypted, it means that the data transmitted between the user’s device and the cellular network is encoded in such a way that only the intended recipient can decipher and understand it.
This process ensures the confidentiality and integrity of the data, protecting it from unauthorized access and tampering.
Moreover, cellular data encryption provides peace of mind to users, knowing that their online activities are shielded from prying eyes. It allows individuals and organizations to confidently communicate, access online services, and conduct financial transactions without the fear of their data being compromised.
Encryption of Cellular Data
Cellular data encryption primarily occurs at two levels: the device level and the network level. Let’s delve into the details of both.
Device Level Encryption
The encryption process starts at the device level, where the user’s smartphone or tablet encrypts the data before transmitting it to the cellular network. This encryption is handled by the operating system and is based on industry-standard encryption algorithms. The data is encrypted on the device using a unique encryption key, making it secure and unreadable if intercepted.
Modern smartphones and tablets typically use robust encryption methods, such as Advanced Encryption Standard (AES) or Rivest Cipher 6 (RC6), to ensure strong encryption and data security. These algorithms are constantly updated and improved to stay ahead of evolving security threats.
It is important to note that the level of encryption may vary depending on the device and its operating system. For example, newer devices and updated operating systems may offer more advanced encryption methods, providing enhanced security for cellular data.
Network Level Encryption
After the data is encrypted at the device level, it is transmitted to the cellular network. The network, in turn, encrypts the data using its own set of encryption protocols. This ensures that even if the data is intercepted during transmission, it remains encrypted and secure.
Cellular networks use various encryption protocols, such as the Global System for Mobile Communications (GSM) algorithm, to safeguard the data during transmission. These protocols are designed to protect data integrity and confidentiality, making it extremely difficult for unauthorized individuals to access or decipher the data.
Additionally, cellular networks employ other security measures, such as user authentication and secure network protocols, to further enhance the overall security of cellular data transmissions.
Is Cellular Data Encryption Foolproof?
While cellular data encryption provides significant security benefits, it is crucial to understand that no security measure is entirely foolproof. Despite the robust encryption methods used, there is always a possibility of vulnerabilities or attacks that can compromise the security of cellular data.
Some common vulnerabilities include flaws in encryption algorithms, weak encryption keys, and sophisticated hacking techniques that target specific devices or network vulnerabilities. Additionally, hackers may use social engineering tactics to gain unauthorized access to a user’s device or network.
To mitigate these risks, users need to stay vigilant and follow best practices for data security. This includes regularly updating device software, using strong and unique passwords, avoiding suspicious websites and downloads, and being cautious of phishing attempts.
Future of Cellular Data Encryption
As technology advances, so does the need for stronger data encryption. With the growing concerns over data breaches and privacy invasions, cellular networks and device manufacturers are continuously working to improve encryption methods and implement advanced security features.
One promising advancement is the adoption of end-to-end encryption, which ensures that even the cellular network provider cannot access the encrypted data. This would provide users with an additional layer of privacy and control over their data.
However, implementing end-to-end encryption on a cellular network scale requires extensive infrastructure upgrades and coordination among network providers.
By staying informed about the latest advancements in cellular data encryption and taking proactive measures to protect their devices and online activities, individuals can continue to enjoy the benefits of cellular connectivity while safeguarding their data.
Implications for Personal Data Security
Cellular data encryption plays a critical role in safeguarding personal data. Let’s explore the implications for personal data security in more detail.
Protecting Sensitive Information
Cellular data encryption ensures that sensitive information, such as login credentials, financial details, and personal messages, remains secure during transmission. By encrypting this data, it becomes nearly impossible for unauthorized individuals to access or decipher it, protecting individuals’ privacy and preventing identity theft.
Safe Online Banking and Shopping
Thanks to cellular data encryption, individuals can confidently engage in online banking and shopping using their smartphones or tablets. The encryption process prevents hackers from intercepting and stealing credit card information, financial transactions, or personal details, providing a secure environment for online financial activities.
Privacy in Communication
Cellular data encryption ensures that communications, such as voice calls, text messages, and video chats, are kept private and inaccessible to third parties. This is crucial in protecting individuals from unauthorized surveillance or interception of their conversations, preserving their privacy and freedom of communication.
Protection Against Malware and Hacking
Encrypted cellular data adds an extra layer of protection against malware and hacking attempts. Even if a user unwittingly accesses a malicious website or downloads an infected file, the encryption ensures that the malware cannot easily access or manipulate the data on the device.
Securing IoT Devices
With the proliferation of Internet of Things (IoT) devices, cellular data encryption becomes even more vital. IoT devices, such as smart home appliances and wearable devices, often transmit and receive sensitive information.
By encrypting the cellular data, users can ensure the security of their IoT devices and protect their personal information from unauthorized access.
Cellular Data Encryption vs. Wi-Fi Encryption
When it comes to data security, it is important to understand the differences between cellular data encryption and Wi-Fi encryption. Let’s compare the two.
Cellular Data Encryption
Cellular data encryption refers to the process of encrypting the data transmitted between a user’s device and the cellular network. It ensures that sensitive information remains secure during transmission, protecting individuals’ privacy and preventing unauthorized access to their data.
Cellular data encryption occurs at the device level and the network level, providing robust security measures for mobile communication.
Benefits of Cellular Data Encryption
- Strong encryption algorithms protect data integrity and confidentiality.
- Provides privacy and security for online activities, such as browsing, messaging, and financial transactions.
- Protects sensitive information from interception and hacking attempts.
- Allows individuals to use cellular networks for communication and data exchange confidently.
Tips for Enhanced Cellular Data Security
- Ensure device software is up to date to benefit from the latest security enhancements.
- Use strong and unique passwords to protect device and network access.
- Avoid connecting to unsecured or suspicious Wi-Fi networks.
- Be cautious of phishing attempts and suspicious links or downloads.
- Regularly review and update privacy settings on apps and devices.
Wi-Fi Encryption
Wi-Fi encryption, on the other hand, refers to the process of encrypting data transmitted over a Wi-Fi network. Wi-Fi encryption protects data while it is being transmitted wirelessly between the user’s device and the Wi-Fi access point. It ensures that unauthorized individuals cannot intercept or access the data transmitted over the network.
Types of Wi-Fi Encryption
Wi-Fi networks can utilize various encryption protocols, such as Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and Wi-Fi Protected Access 2 (WPA2). These protocols offer different levels of security and encryption strength, with WPA2 being the most secure and widely adopted.
Benefits of Wi-Fi Encryption
- Ensures data transmitted over Wi-Fi networks is secured from interception.
- Protects sensitive information, such as passwords and personal details, from unauthorized access.
- Allows individuals to safely use public Wi-Fi networks without compromising their privacy.
- Prevents hackers from accessing and manipulating data transmitted over the network.
Tips for Enhanced Wi-Fi Security
- Use WPA2 or higher encryption protocols for Wi-Fi networks.
- Create a strong and unique Wi-Fi password.
- Disable remote management of Wi-Fi routers to prevent unauthorized access.
- Avoid connecting to unsecured public Wi-Fi networks or use a virtual private network (VPN) for added security.
- Regularly update Wi-Fi router firmware to benefit from security patches and enhancements.
Cellular data encryption is a vital component of data security, ensuring the privacy, integrity, and confidentiality of our online activities. Through robust encryption algorithms and secure protocols, cellular data encryption protects sensitive information, enables safe communication, and safeguards personal data in an increasingly connected world.
By understanding the importance of cellular data encryption and following best practices for data security, individuals can enjoy the benefits of cellular connectivity while staying protected from malicious actors and privacy infringements.
Frequently Asked Questions
Welcome to our frequently asked questions section on cellular data encryption. In this section, we address common queries related to the security and privacy of cellular data. Read on to find answers to your questions.
1. How secure is cellular data transmission?
Cellular data transmission, such as mobile internet or data exchanged during calls, is generally encrypted to ensure security and protect user privacy. Network providers and device manufacturers employ encryption protocols to safeguard data during transmission. This encryption makes it difficult for unauthorized individuals to intercept and access the data.
However, it’s worth noting that the level of security can vary depending on factors like the encryption algorithm, device, and network provider. It is always recommended to follow best practices like using secure networks, keeping devices up-to-date, and utilizing additional security measures, such as VPNs, to enhance the security of your cellular data.
2. Can cellular data be intercepted and decrypted?
While cellular data is generally encrypted, it is not entirely immune to interception and decryption. Sophisticated hackers with specialized tools and techniques may be able to intercept and decrypt cellular data under certain circumstances. However, such instances are relatively rare and typically require advanced knowledge and access to specific equipment.
To mitigate the risk of interception, network providers continuously work on improving their encryption protocols and addressing any vulnerabilities that may arise. By staying updated with the latest security updates and ensuring your network provider follows industry-standard encryption practices, you can minimize the chances of your cellular data being intercepted and decrypted.
3. Does cellular data encryption protect against attacks on the device itself?
Cellular data encryption primarily focuses on securing data during transmission through the network. It does not directly protect against attacks on the device itself, such as malware or physical device compromise. Device security relies on separate measures, including installing security updates, using strong passwords or biometric authentication, and being cautious of suspicious apps or websites.
While cellular data encryption plays a crucial role in protecting data during transmission, it is essential to implement comprehensive device security measures to safeguard against other potential threats that may compromise your data.
4. Is all cellular data encrypted, regardless of the type of connection?
Cellular data encryption applies to various types of connections, including 2G, 3G, 4G, and 5G. All these technological generations utilize encryption to some extent, with the level of security generally increasing with each subsequent generation. However, it’s important to note that not all cellular network protocols provide the same level of encryption, and older technologies like 2G may have weaker encryption than the more advanced 4G or 5G networks.
When using cellular data, it is advisable to connect to networks that offer stronger encryption, such as 3G, 4G, or 5G, whenever possible, to benefit from higher levels of security during data transmission.
5. Are there any additional steps I can take to enhance the security of my cellular data?
Absolutely! Apart from relying on the cellular network provider’s encryption protocols, you can take additional steps to enhance the security of your cellular data. Some measures include:
– Using Virtual Private Networks (VPNs) to encrypt your data further and protect your privacy.
– Avoiding insecure public Wi-Fi networks and opting for trusted cellular networks whenever possible.
– Keeping your devices updated with the latest security patches and firmware releases.
– Avoid downloading apps from untrusted sources and regularly reviewing app permissions.
By implementing these additional security measures, you can add an extra layer of protection to your cellular data and ensure a more secure digital experience.
Cellular data is generally encrypted, which means it is protected from unauthorized access. Encryption is like putting a secret code on your messages, so only the intended recipient can understand them. However, it’s important to remember that not all apps or websites use encryption, so it’s wise to be cautious about sharing sensitive information over the internet.
In some cases, your cellular data may not be encrypted if you’re using a public Wi-Fi network or if you’re visiting a website that doesn’t have proper security measures in place. It’s always a good idea to use a virtual private network (VPN) or stick to trusted websites and apps to ensure your data stays safe. Overall, while cellular data is generally encrypted, it’s still important to stay vigilant and be mindful of your online activities.